Friday, 24 January 2014
Sunday, 26 May 2013
Zemana Antilogger 1.9.3.444 GIVEAWAY
0
Zemana Antilogger GIVEAWAY
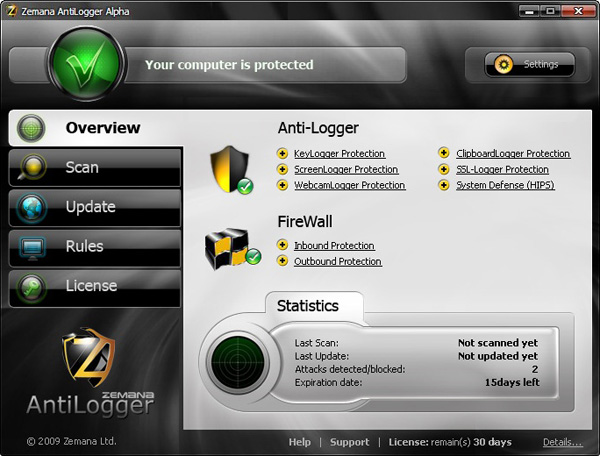
Zemana AntiLogger Features:
SSL Logger protection: (WORLD FIRST!) 128-bit encryption reliably secures data during online shopping and high-value financial transactions. Unfortunately, a new generation of spyware grabs your data just before it becomes safely encrypted!
Zemana AntiLogger's unique proactive protection prevents your personal information from being stolen while you are conducting online banking transactions or e-commerce using an encrypted 128-bit SSL (Secure Socket Layer).
Webcam Logger protection: (WORLD FIRST!) Is Big Brother watching you? Hackers and spyware can seize control of your webcam, even when it's switched off! Needless to say, Zemana AntiLogger prevents this.
Key Logger protection: Keyloggers record whatever you type by monitoring the keyboard. This renders most security useless, but not Zemana AntiLogger!
Clipboard Logger protection: Copying, cutting and pasting sends potentially sensitive data to your Windows clipboard where malware can get at it. Fortunately, Zemana AntiLogger deals with all attempts at malicious monitoring, including memory capture.
Screen Logger protection: Just as you can take a screen capture, screenlogger malware snaps the screen at your most vulnerable moments, e.g., when you are plugging in sensitive data such as bank account information with VirtualKeyboard. Zemana Anti-Screen Logger spots this suspicious activity in ways that go beyond the standard, signature-based anti-logging algorithms.
System Defense: Malware likes to get at your registry, your physical memory (RAM), and other sensitive areas so it can inject malicious code and seize control of your PC. Zemana AntiLogger guards against all this, securing the very heart of your machine.
Protection Highlights
No need to download latest signatures: Unlike old-fashioned antivirus and anti-spyware products, AntiLogger does not wait to receive malware signatures in order to prevent malware attacks. You never have to worry about getting the latest update.
Compatible with commonly used security software: Signature-based anti-malware, personal firewall, disk encryption, and many other client security tools can continue to operate normally with AntiLogger.
Proactive Modules: Monitors installation, registry and file changes, spotting and stopping all suspicious behavior.
Bulletproof self-defense: AntiLogger cannot be deactivated by targeted attacks, ensuring continuity of protection.
Why Anti-Spyware Is Important
0
Why is Anti-Spyware Important ??
Whether you’re aware of it or not, somebody can be watching every move you make on your computer. Such a person is said to be a computer spy. It doesn’t matter if you’re jumping from site to site online, checking your email, or typing up a document in your word processor, you may be watched. How is this done? Through a software program referred to as spyware. Worst of all, you remain unaware that it is happening.
Why do people spy on innocent computer users? What do they care about your personal computer habits? Spies seek information as to who you are, where you live, what you do on your computer, and what sites you frequent online. With the data they gather, they take it and sell it to third parties as a source of income. Worst of all, they do it in an underhanded, immoral, and often illegal manner while invading your privacy.
Spyware, also called malware, installs itself on your computer without you even knowing about it. With it, facts are accumulated about your personal computing habits and this information is being sold to advertising firms whom push unwanted ads at you. It all happens as these malicious programs record you keystrokes and send them to a third party. This is how thieves get your usernames and passwords.
Not only does spyware intrude on your personal privacy, it may wreak havoc with your computer. It can clog your system’s memory, consume space on your hard drive, and cause performance slowdowns. Spyware can even create an electronic “back door” enabling bad people to come into your system, take control of it, and use it for their own purpose. Your machine can be a vehicle to sending spam to others or launching attacks on other computers on the internet.
And if that isn’t enough, spyware can change settings and hijack your web browser causing an unwanted homepage to appear every time you get online. Some of these malicious programs can cleverly embed themselves so deeply into your system that you will need a great deal of computer expertise to remove them. This may necessitate bringing your computer to a “geek squad” for repairs.
How does spyware find its way into your computer? Through the following ways:
- It arrives in an automatic download form from a website you are surfing, known as “drive-by downloading.” Porn sites or the like can be a chief source of spyware.
- You can be tricked into clicking on a link that downloads spyware from a website.
- Pop-up windows telling you that you won a prize are a common example.
- Spyware can be embedded in the installation of a free or pirated piece of software you download. Peer-to-peer (P2P) sites that offer shared MP3 and video files such as Kazaa are more than likely to transmit spyware when installing them.
- Spyware can be found in email attachments from senders you don’t even know. Such attachments come in commercial email and are deemed as spam.
There are numerous types of programs that contain spyware and the sad part is, they are commonly downloaded online. Such programs are desktop toolbars; free games, puzzles, or other forms of entertainment; screensavers, pop-up blocker programs; and files from file-sharing sites.
Computer spying is practiced by companies as well as devious people. Individuals seek out information submit to businesses in exchange for money. Businesses either buy private data and/or use spyware themselves. By analyzing your personal computer using habits, they can solicit ads for products or services you are likely to buy. As you jump onto the Internet, you will encounter pop-up ad boxes. Such software that creates pop-up advertisements is call adware and is a part of spyware.
Adware is often bundled with free software. Publishers include it as a means of earning additional revenue. The presence of adware is often written in the End User License Agreement (EULA). The EULA typically is a long scrollable document one must read and accept the terms before the program can be installed. Hence, it is highly recommended that you at least skim over the EULA before clicking “NEXT.”
Yet, another form of spyware “hijacks” browsers. If this spyware is installed on your machine and you hop onto the Internet, rather than your favorite homepage coming up, you’ll see a rogue page instead. More than likely this page will be an affiliate link. Affiliate links lead to pages where those who posted them earn money each time they’re visited. Likewise, there will be other inviting links and if you click on one of them, you’ll land on yet another affiliated page. The settings in the spyware override the settings you made on your machine.
Browser hijacking is a legitimate way of making money, but is exploited by private individuals as well. Some have directed surfers to pages that closely resemble those posted by Yahoo or Google. The site “Cool Web Search” is a Russian based site that is a classic example. Its owners claim that they stop hijackers that post affiliated sites. Giving viewers a false sense of security, they’ve made themselves a name: CWS hijackers.
Worst of all, some spywares can embed themselves so deeply into your computer that you will need a high degree of computer expertise to remove them. Some may take total control of your computer and the next time you start it up, it will automatically get online to that affiliated page.
Therefore, it is important that you remove spyware from your computer with an antispyware program. If you are having extreme difficulty navigating on the Internet or even in your operating system, chances are, you have spyware. You may see annoying pop-up boxes that are hard to get rid of. At this point yhttp://www.blogger.com/img/blank.gifou’ll want to disconnect your computhttp://www.blogger.com/img/blank.gifer from you home network and the Internet before it has a chance to spread to other computers. Consult your administrator or bring your computer into a shop for repairs.
Detect Hidden Trojans on Your Computer
0
Detect Hidden Trojans on Your Computer
Learn How to Detect Hidden Trojans/Viruses/Keyloggers on Your PC
Are you beware that there is a hidden Trojan, Virus or Keylogger working on your PC and sending your logins to hackers?
If you are in that situations you don't need to worry anymore. In this post i will show you a security software called Process Revealer that can detect and kill hidden processes.

Process Revealer Free Edition is a free hidden process detector that reveals what does not appear in standard detection utilities like Windows Task Manager. Process Revealer provides detailed information about each process running on your computer to help you know if a process is related to a malicious program. Hidden programs are automatically highlighted in the interface and can be removed in one click.
Download Process Revealer Free Edition
Do you have questions, comments, or suggestions? Feel free to post a comment!
How to Surf The Internet Without Any Browser
0
How to Surf The Internet Without Any Browser
Ever find yourself sitting in front of a computer where Internet Explorer or Firefox was blocked by IT Administrator, and restricted you from installing any software? If that PC is running Windows XP, then there is chance for you to still surf Internet. Just follow these simple steps:
1. Open Calculator, Start> Program Files> Accessories> Calculator or press Windows+R and type 'calc' in the run box, click OK.
2. In Calculator, go to Help> Help Topics.
3. Right click on the left hand side of the title bar and click on 'Jump to URL'.
4. Type in the URL and make sure include the 'http://' at the beginning.
Note: Basically what you are looking at is Internet Explorer 6 inside a help window, but this version of program isn’t quite smart as Internet 6. This was tested in Windows XP SP2 with Internet Explorer 6 and I’m not sure whether it will works in Internet Explorer 7 installed computer.
1. Open Calculator, Start> Program Files> Accessories> Calculator or press Windows+R and type 'calc' in the run box, click OK.
2. In Calculator, go to Help> Help Topics.
3. Right click on the left hand side of the title bar and click on 'Jump to URL'.
4. Type in the URL and make sure include the 'http://' at the beginning.
Note: Basically what you are looking at is Internet Explorer 6 inside a help window, but this version of program isn’t quite smart as Internet 6. This was tested in Windows XP SP2 with Internet Explorer 6 and I’m not sure whether it will works in Internet Explorer 7 installed computer.
Subscribe to:
Comments (Atom)